The vulnerability was identified and fixed in 2013 but in 2014 Microsoft revised the fix allowing Malsmoke hackers in 2022 to spread ZLoader malware.
Israel-based cybersecurity firm Check Point Research has been assessing a sophisticated infection chain since Nov 2021. Researchers have now published their report, stating that a new ZLoader malware campaign is underway and has already stolen data and credentials of more than 2000 victims across 111 countries as of 2 Jan 2022.
In the new campaign, attackers exploit remote monitoring tools and a 9-year-old flaw in Microsoft’s digital signature verification (CVE-2013-3900) to steal user passwords and sensitive personal data.
What is ZLoader?
ZLoader, is a banking Trojan. It utilizes web injection to steal passwords, browser cookies, and sensitive user data and is suspected of delivering Ryuk and Conti ransomware variants.
In previous incidents involving ZLoader, the trojan was delivered through traditional phishing email campaigns as well as by abusing online advertising platforms.
About the Campaign
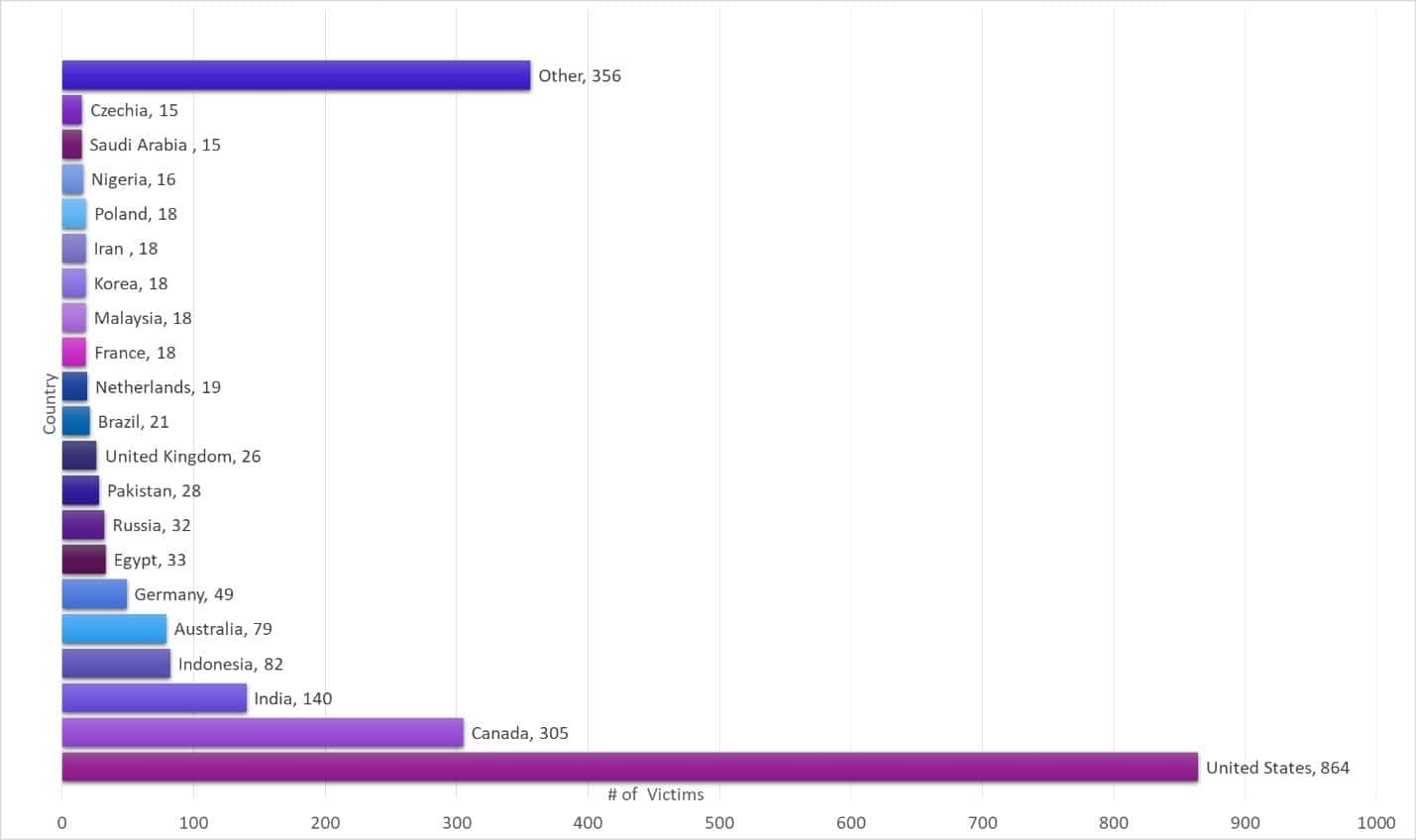
Users in the USA, Canada, Australia, India, and Indonesia are primarily impacted by this campaign. According to Check Point researchers, malware is hidden under several layers of obfuscation and other detection bypass methods to prevent discovery.
The attack commences after the attacker gains initial access through installing a legit enterprise remote monitoring software known as Atera, pretending to be a Java installation. The attacker gains full access to the targeted system.
The attacker then uploads/downloads arbitrary files and executes malicious scripts. Then it exploits Microsoft’s digital signature verification mechanism to inject ZLoader payload. However, the distribution mode of this installer is yet known.
“The techniques incorporated in the infection chain include the use of legitimate remote management software (RMM) to gain initial access to the target machine. The malware then exploits Microsoft’s digital signature verification method to inject its payload into a signed system DLL to further evade the system’s defenses,” Golan Cohen from Check Point wrote in a blog post.
Microsoft Signature Validation Vulnerability Exploited
Check Point researchers state that the cybercrime group Malsmoke is responsible for the newly identified ZLoader campaign. The attackers exploited an old WinVerifyTrust signature validation vulnerability, which lets remote attackers execute arbitrary code through specially designed portable executables by modifying the malicious code snippet without affecting the signature’s validity.
Microsoft fixed the bug in 2013 but revised it in July 2014, after which it stopped enforcing stricter verification mechanisms as a default functionality on compatible new versions of MS Windows.
“In other words, this fix is disabled by default, which is what enables the malware author to modify the signed file,” Cohen added.
Users must exercise caution, never try to install programs from unknown or unofficial sources, and avoid clicking on links or attachments in suspicious emails.

