Researchers have discovered critical vulnerabilities in the UEFI firmware from InsydeH2O used by multiple computer vendors such as Fujitsu, Intel, AMD, Lenovo, Dell, ASUS, HP, Siemens, Microsoft, and Acer.
UEFI (Unified Extensible Firmware Interface) software is an interface between a device’s firmware and the operating system, which handles the booting process, system diagnostics, and repair functions.
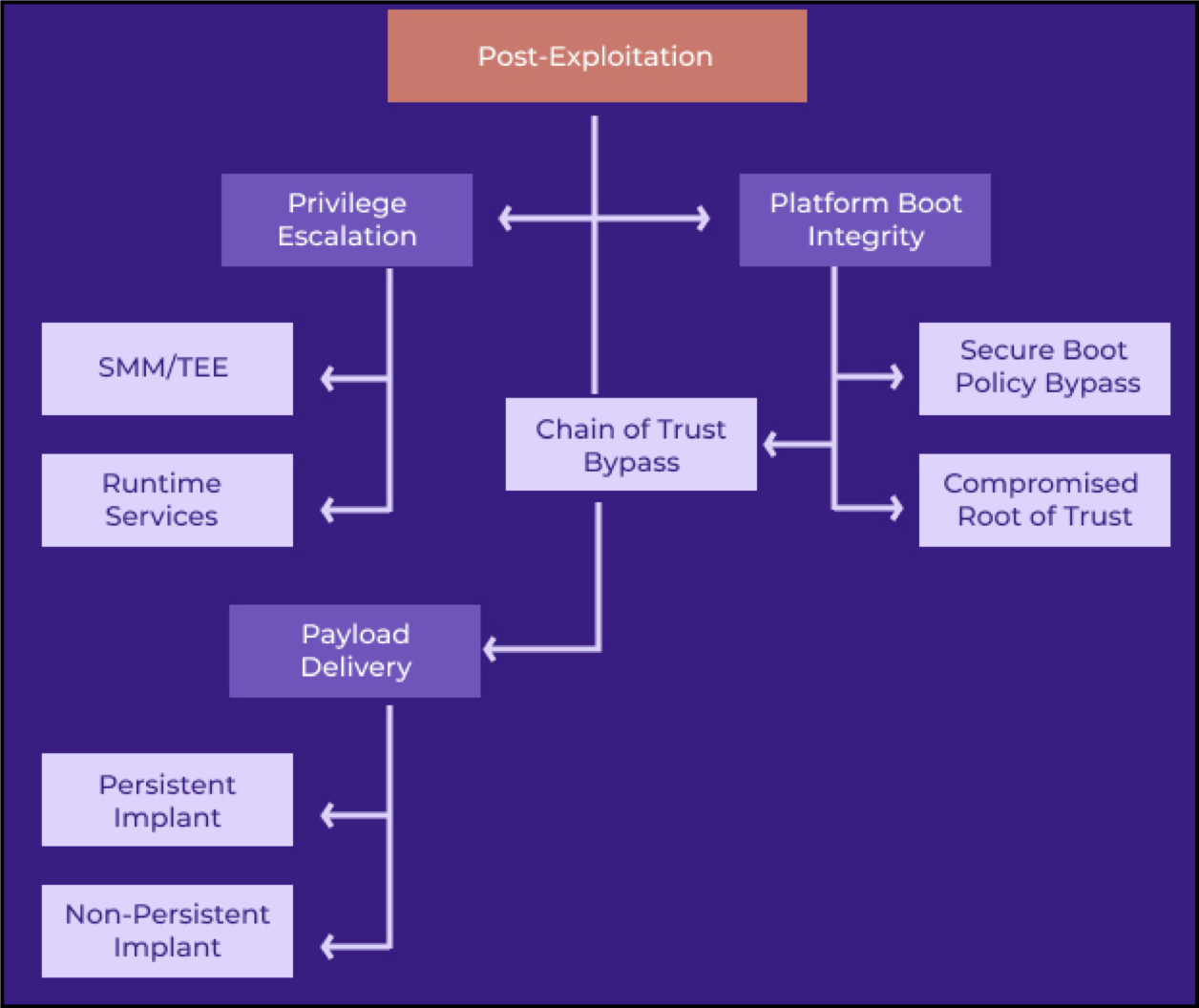
In total, 23 flaws were found in the InsydeH2O UEFI firmware, most of them in the software's System Management Mode (SMM) that provides system-wide functions such as power management and hardware control.
SMM’s privileges exceed those of the OS kernel, so any security issues in this space can have severe consequences for the vulnerable system.
More specifically, a local or remote attacker with administrative privileges exploiting SMM flaws could perform the following tasks:
- Invalidate many hardware security features (SecureBoot, Intel BootGuard)
- Install persistent software that cannot be easily erased
- Create backdoors and back communications channels to steal sensitive data
The 23 flaws are tracked as: CVE-2020-27339, CVE-2020-5953, CVE-2021-33625, CVE-2021-33626, CVE-2021-33627, CVE-2021-41837, CVE-2021-41838, CVE-2021-41839, CVE-2021-41840, CVE-2021-41841, CVE-2021-42059, CVE-2021-42060, CVE-2021-42113, CVE-2021-42554, CVE-2021-43323, CVE-2021-43522, CVE-2021-43615, CVE-2021-45969, CVE-2021-45970, CVE-2021-45971, CVE-2022-24030, CVE-2022-24031, CVE-2022-24069.
Of the above, CVE-2021-45969, CVE-2021-45970, and CVE-2021-45971 in the SMM are rated with critical severity, receiving a 9.8 score out of 10.
Ten of the discovered vulnerabilities could be exploited for privilege escalation, twelve memory corruption flaws in SMM, and one is a memory corruption vulnerability in InsydeH2O's Driver eXecution Environment (DXE).
Insyde Software has released firmware updates to fix all identified security vulnerabilities and published detailed bulletins to assign severity and description for every flaw.
However, these security updates need to be adopted original equipment manufacturers (OEMs) and pushed to affected products.

