The Digital Security Authority (DSA) wants to bring to your attention a vulnerability affecting Palo Alto Networks PAN-OS software.
Technical Details
An authentication bypass in the Palo Alto Networks PAN-OS software enables an unauthenticated attacker with network access to the management web interface to bypass the authentication otherwise required by the PAN-OS management web interface and invoke certain PHP scripts. While invoking these PHP scripts does not enable remote code execution, it can negatively impact integrity and confidentiality of PAN-OS
The risk is greatest if you enabled access to the management interface from the internet or any untrusted network either:
- Directly or
- Through a dataplane interface that includes a management interface profile.
You greatly reduce the risk if you ensure that you allow only trusted internal IP addresses to access the management interface. Palo Alto Networks has observed exploit attempts chaining CVE-2025-0108 with CVE-2024-9474 and CVE-2025-0111 on unpatched and unsecured PAN-OS web management interfaces.
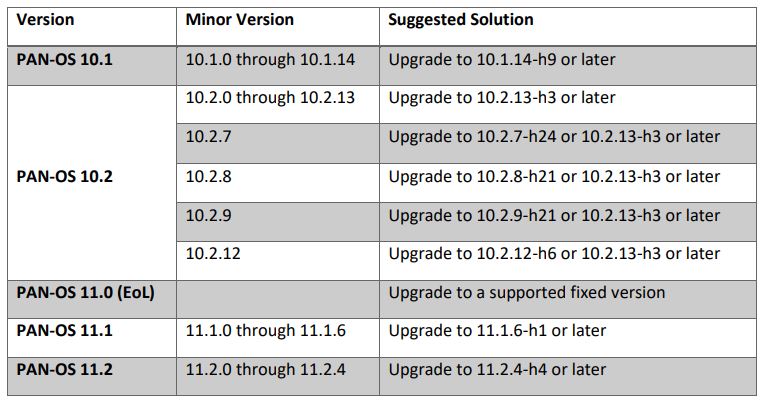
Affected Products:

Recommendations
The Digital Security Authority recommends updating the affected product version by applying the fixed release as its showned below:
References
The information presented in this report is based on available data up to the 19th of February 2025.

