Tens of thousands of QNAP network-attached storage (NAS) devices are waiting to be patched against a critical security flaw addressed by the Taiwanese company on Monday.
Remote threat actors can exploit this SQL injection vulnerability (CVE-2022-27596) to inject malicious code in attacks targeting Internet-exposed and unpatched QNAP devices.
QNAP also assigned this bug a CVSS base score of 9.8/10 and said it could be abused in low-complexity attacks by unauthenticated malicious actors without requiring user interaction.
The company recommends customers with impacted devices (running QTS 5.0.1 and QuTS hero h5.0.1) to upgrade to QTS 5.0.1.2234 build 20221201 or later and QuTS hero h5.0.1.2248 build 20221215 or later to secure them from attacks.
To update your device, you have to log in as the admin user, go to "Control Panel → System → Firmware Update," click the "Check for Update" option under the "Live Update" section and wait for the download and installation to complete.
While QNAP hasn't tagged this flaw as being actively exploited in the wild, customers are advised to update to the latest available software version as soon as possible since NAS devices have a long history of being targeted in ransomware attacks.
Tens of thousands of unpatched devices exposed to attacks
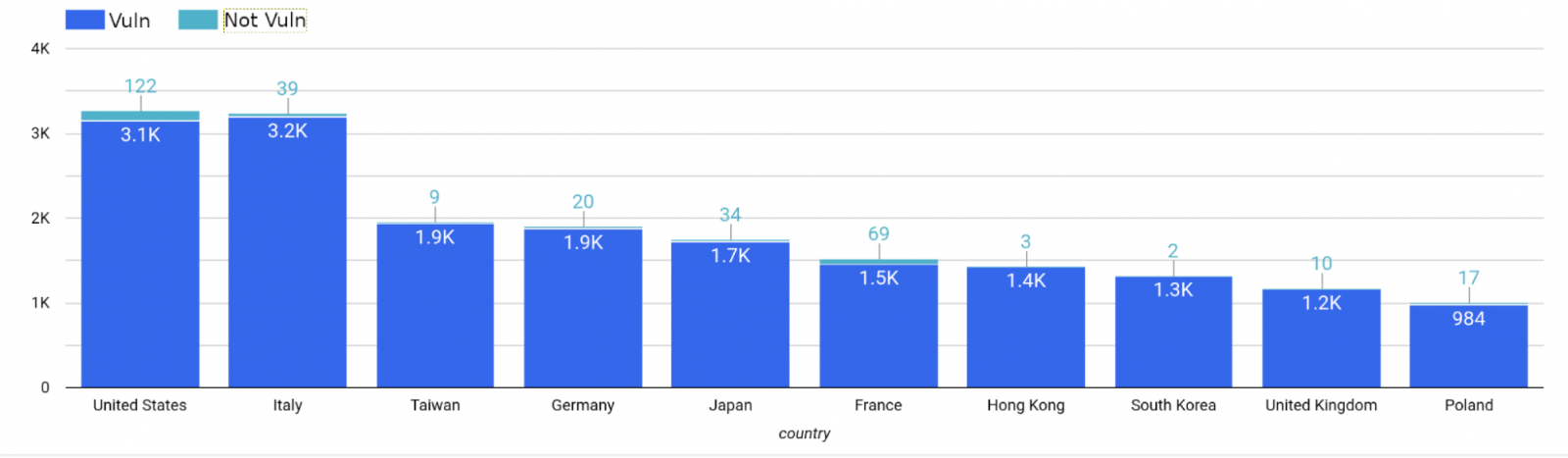
One day after QNAP released security updates to address this critical vulnerability, Censys security researchers published a report revealing that just over 550 out of more than 60,000 QNAP NAS devices they found online were patched.
Luckily, since this flaw is not yet abused in the wild and proof-of-concept exploit code hasn't yet surfaced online, there's yet time to patch these vulnerable NAS devices and secure them from attacks.
Given that such devices have been targeted with multiple ransomware strains in recent years (including Muhstik, eCh0raix/QNAPCrypt, QSnatch, Agelocker, Qlocker, DeadBolt, and Checkmate), it's worth repeating that QNAP customers should immediately patch their NAS device before threat actors pounce and encrypt their files.
If the exploit is published and weaponized, it could spell trouble to thousands of QNAP users. Everyone must upgrade their QNAP devices immediately to be safe from future ransomware campaigns.
Besides updating your NAS device ASAP, you should also consider not exposing it online to ensure it's not reachable via the Internet for remote exploitation.
The NAS maker has previously urged customers with Internet-exposed devices to take the following measures to defend them from incoming attacks:
- Disable the Port Forwarding function of the router: Go to the management interface of your router, check the Virtual Server, NAT, or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 433 by default).
- Disable the UPnP function of the QNAP NAS: Go to myQNAPcloud on the QTS menu, click the "Auto Router Configuration," and unselect "Enable UPnP Port forwarding."
You should also toggle off SSH and Telnet connections, change the system port number, change device passwords, and enable IP and account access protection using these detailed step-by-step procedures.


