The newly revealed USBCulprit malware is used by a group known as Cycldek, Conimes, or Goblin Panda and is designed for compromising air-gapped devices via USB.
Cycldek is a Chinese APT group targeting that has been Southeast Asian nations for a long time to steal government information and state secrets.
The APT group has demonstrably taken an interest in “large organizations and government institutions in Vietnam,” stated a new report on the malware by Kaspersky.
For example, in 2013, the security firm CrowdStrike reported how the group was hacking “defense, energy, and government sectors” in conflicted Southeast Asian territories. At the time, the group had leveraged CVE-2012-0158 exploits to drop malware via malicious Microsoft Word documents.
In the years following the incident, the group continued to expand their arsenal of APTs, such as using rich-text format (RTF) documents with political content to deploy Remote-Access Trojans (RATs).
What Kaspersky revealed this week is a custom-designed stealthy tool called ‘USBCulprit’, which has sophisticated information-leeching capabilities, especially when used on an air-gapped system.
It enters the system via RTF documents or other unknown means, performs an extensive scanning of the victim’s system, and begins to leech documents, passing them and replicating itself onto removable media.
“This tool, which we saw downloaded by RedCore implants in several instances, is capable of scanning various paths in victim machines, collecting documents with particular extensions and passing them on to USB drives when they are connected to the system. It can also selectively copy itself to a removable drive in the presence of a particular file, suggesting it can be spread laterally by having designated drives infected and the executable in them opened manually,” Kaspersky explains.
RedCore and BlueCore are terms used by Kaspersky to describe the two different styles (variants) of malware deployed by the group. Initial Infection Vector for BlueCore has been listed as “RTF documents,” whereas that for RedCore is still unknown.
Kaspersky’s report shows a comprehensive diagram of how the two variants RedCore and BlueCore actuate and share information, in the form of a well-coordinated “cluster.”
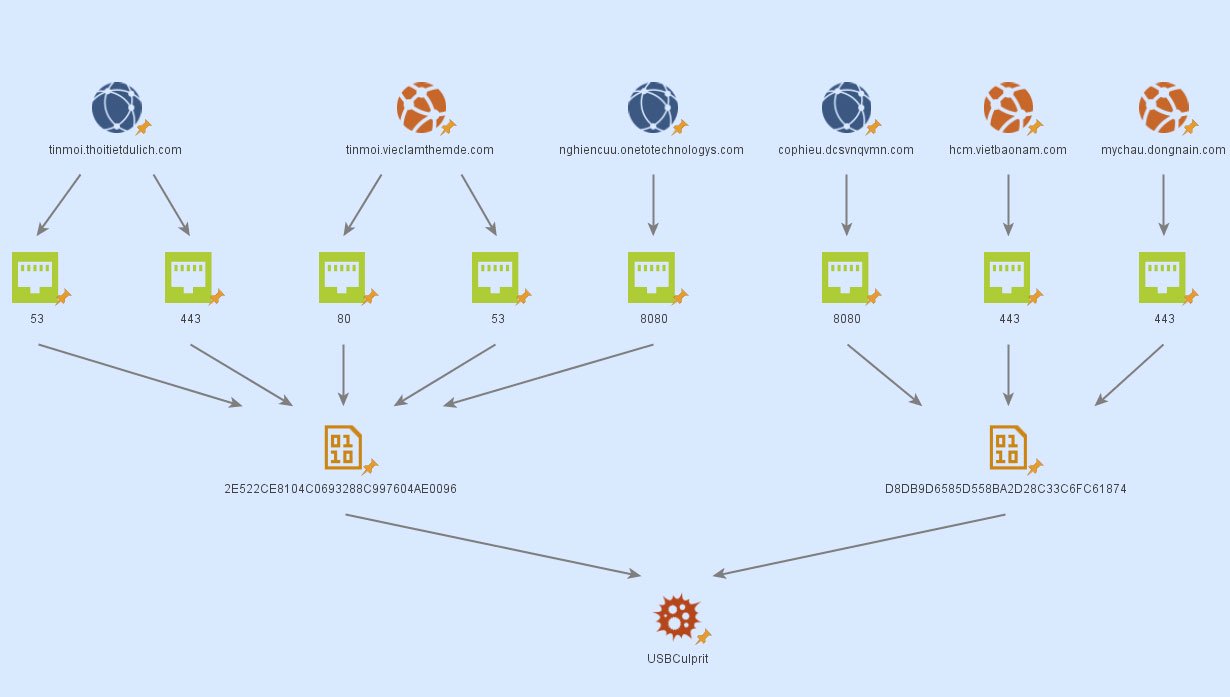
Both of these variants have been attributed to the Cycldek threat actor group.
“Furthermore, considering both differences and similarities, we are able to conclude that the activities we saw are affiliated to a single actor, which we refer to as Cycldek. In several instances, we spotted unique tools crafted by the group that were downloaded from servers of both groups… All in all, this suggests the entities operating behind those clusters are sharing multiple resources – both code and infrastructure – and operating under a single organizational umbrella.”
Uses USB drives to steal data
USBCulprit runs stealthily at regular time intervals, monitoring for removable media, and looking for opportunities to replicate itself:
“When bootstrapping and data collection is completed, the malware attempts to intercept the connection of new media and verify that it corresponds to a removable drive. This is achieved by running an infinite loop, whereby the malware is put to sleep and wakes at constant intervals to check all connected drives with the GetDriveTypeW function. If at least one is of type DRIVE_REMOVABLE, further actions are taken,” Kaspersky explained.
To determine the direction and sequence of devices to copy data from and into, a USBCulprit “cluster” is equipped with advanced traversal and lateral movement capabilities.
When stealing files, the malware plants file markers (e.g. “1.txt”, “2.txt”, and so on) on drives to indicate which direction the data exfiltration should flow.
“As part of the same loop mentioned above, the existence of another marker file named ‘2.txt’ will be checked locally to decide if lateral movement should be conducted or not. Only if this file exists, will the malware’s binary be copied from its local path to the ‘$Recyc1e.Bin’ directory,” stated Kaspersky.
The stealthy activities undertaken by malware hint toward its practical application in exfiltrating sensitive data from air-gapped devices as USB devices are plugged into them.
Having already been used to target several Southeast Asian high-profile organizations, attacks like USBCulprit demonstrate how sophisticated APTs can breach anything; even air-gapped devices.
USBCulprit indicators of compromise (IOCs), domains, and hashes of other malware have been made available by Kaspersky in the same advisory.
The information contained in this website is for general information purposes only. The information is gathered from Bleeping Computer, while we endeavour to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the website or the information, products, services, or related graphics contained on the website for any purpose. Any reliance you place on such information is therefore strictly at your own risk. Through this website, you are able to link to other websites which are not under the control of CSIRT-CY. We have no control over the nature, content and availability of those sites. The inclusion of any links does not necessarily imply a recommendation or endorse the views expressed within them. Every effort is made to keep the website up and running smoothly. However, CSIRT-CY takes no responsibility for, and will not be liable for, the website being temporarily unavailable due to technical issues beyond our control.


